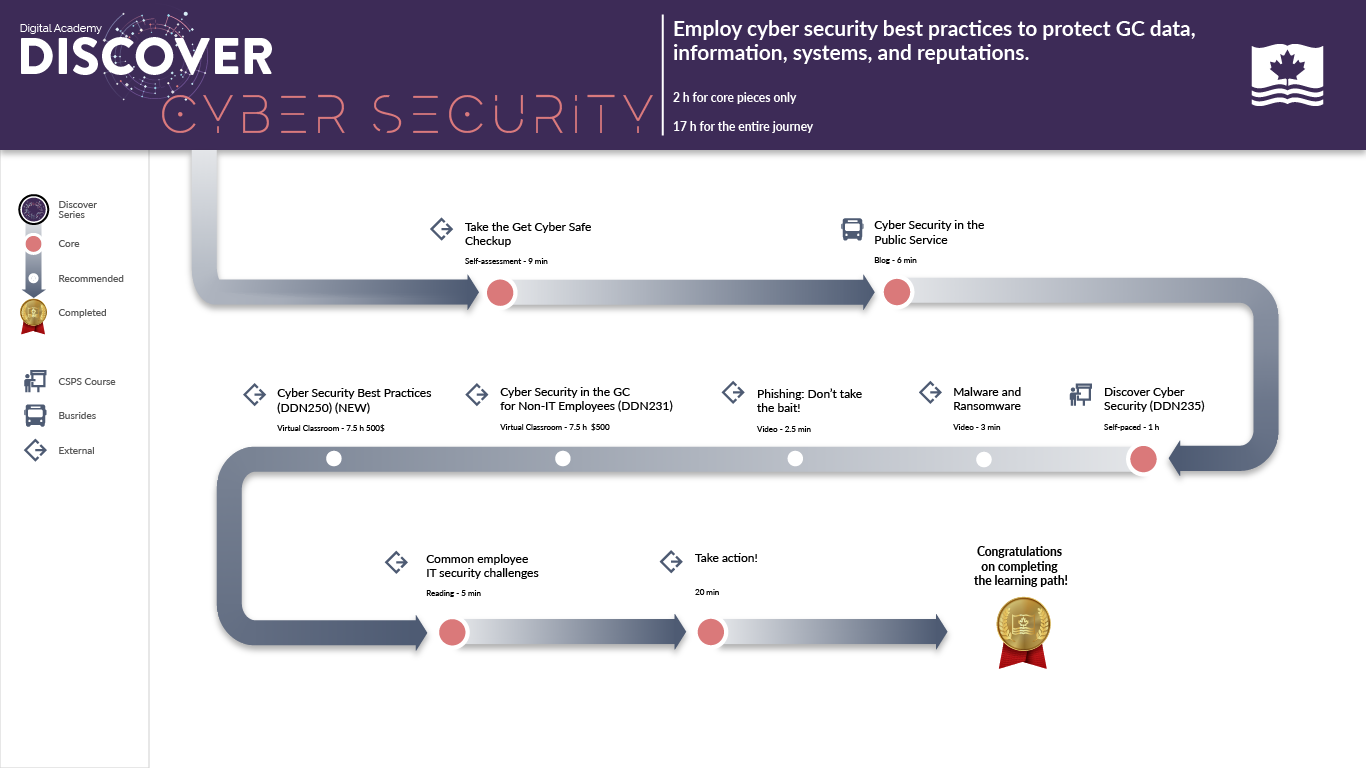
Start your Discover Cyber Security journey
We’ve recommended five core and three recommended foundational learning experiences in the Discover Cyber Security learning path for all public servants. Consume them in the suggested order to achieve the best learning outcomes. Once you’ve completed the core products, we encourage you to look at the additional learning products to get the most out of this experience.
Employ cyber security best practices to protect Government of Canada (GC) data, information, systems, and reputations.

Core and Recommended Learning
This classroom course was designed by the Cyber Centre Learning Hub at the Canadian Centre for Cyber Security and has a cost of $500. Link will take you directly to the Learning Hub web page.
This classroom course was designed by the Cyber Centre Learning Hub at the Canadian Centre for Cyber Security and has a cost of $500. Link will take you directly to the Learning Hub web page.
Set aside some time now to implement what you’ve learned. Start by:
- adding multi-factor authentication to your accounts
- making your passwords (or, better yet, passphrases) unique, strong, and random
- customizing your privacy settings
Here’s a handy checklist to help you. (20 minutes)

Building a love of learning about cyber security? We’ve recommended some additional learning experiences in the Discover Cyber Security learning path. Keep your Discover Cyber Security journey going in a format that interests you!

Keep the Learning Going
Micro-learning: Articles, blogs and videos
Courses
This classroom course was designed by the Cyber Centre Learning Hub at the Canadian Centre for Cyber Security and has a cost of $500. Link will take you directly to the Learning Hub web page.
Congratulations!
You have completed the Discover Cyber Security learning path. You should be able to describe what cyber security is and why it’s important, recognize the impact of poor cyber practices, and practise consistently safe cyber behaviour. After learning more about cyber security and why it matters, be sure to make some key changes to your own cyber behaviour.

Next steps
Future learning opportunities
Subscribe to our newsletter. We’re sharing new digital courses, events, micro-learning and more straight to your inbox. Sign up to keep up with digital trends, skills, and resources for public servants like you.
Discover other learning paths
Connect with like-minded public servants
Join the Canadian Digital Gov Connections space on Slack.